Intelbroker, targeting Hewlett-Packard Enterprise (HPE), claiming that it can access the company’s internal infrastructure, and argues that it will sell it to access instead of selling data.
Intelbroker, a notorious hacker linked to a previous famous cyber attack, has announced suspected data violation of Hewlett-Packard Enterprise (HPE). The hacker claims that it has been cloned by accessing new data from the HPE repository.
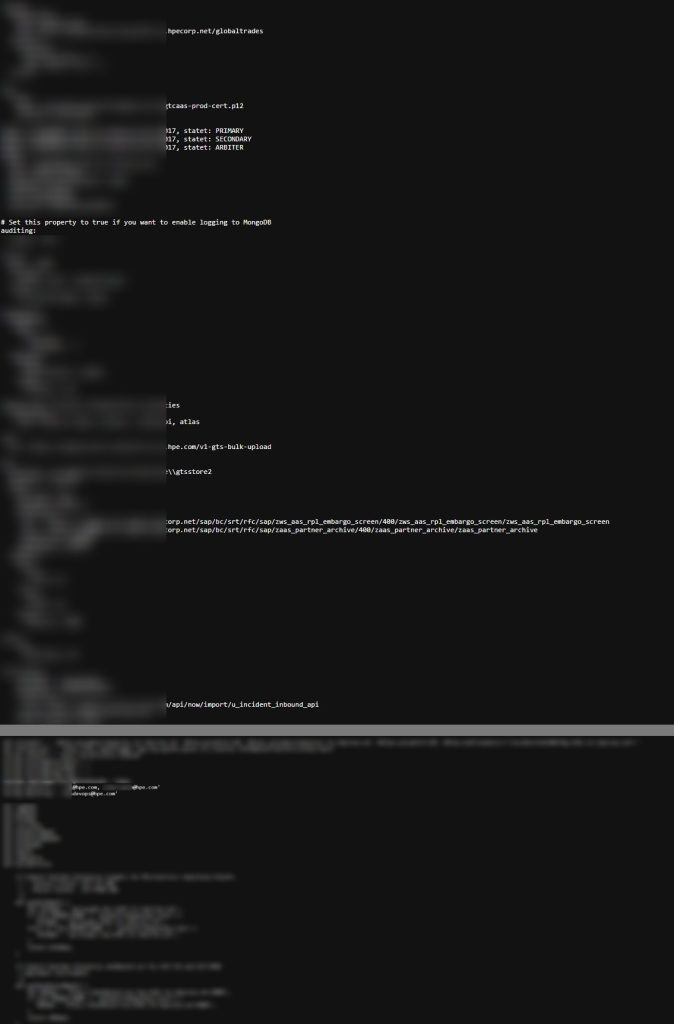
The size of the data charged is 500 MB, but it is relatively smaller than usual, but the screenshot shared only with hackread.com provides insights on what looks like an infringed infrastructure. , Reveal the published qualification information, internal configuration, and unique source code.
This latest violation is the second violation of Intelbroker targeting Hewlett Packard Enterprise. In January 2025, as reported by Hackread.com, Intelbroker publicly asserted the responsibility for damaged HPE infrastructure in a previous attack. The violation disclosed through the violation forum and the exclusive conversation with hackread.com included the substantial removal of confidential data.
The latest claim
According to the quick analysis of data trees and internal screenshots seen by hackread.com, the unique source of HPE products such as some confidential data, ILO and Zerto systems, internal Git repository, and Docker build, such as private keys and certificates. It pointed out the possibility of extracting code.
In addition, the data tree has access to exposed infrastructure configurations such as internal services and endpoints, such as internal services and Salesforce integration, internal DNS, deployment pipeline, etc. It is said that it was done.
Plan to sell access
First of all, on suspicion of HPE violation, Intelbroker provided stolen data for sales and maintained anonymous by requesting payment at Monero Cryptocurrency. However, this time, the hackers argue that the entire dataset will be released for free and will sell access.
“I don’t know if I will sell data. It may only leak it for free this time, but I don’t know yet, but my team may have sold access to HPE infrastructure.
Intelbroker told Hackread.com.
Nevertheless, the new HPE data violation has shown an urgency for the organization to secure infrastructure, regularly audit access control, and monitor suspected activities. When verified, this violation represents the main case of HPE and has a long -term effect on management and customer trust.
HPE is not HP Inc.
Hewlett-Packard Enterprise (HPE) and HP Inc. are two separate entities that occurred from the split of Hewlett-Packard in 2015. HPE focuses on enterprise -level IT solutions, including servers, storage, networking, cloud computing, and software services. For companies.
In contrast, HP Inc. specializes in consumers and small and medium -sized enterprises and specializes in personal computing devices and printer. They share common origin, but their operation and focus area are completely different.
hackread.com contacted HPE for a statement. The answer from the company will be added to this article as soon as it is received. Look forward to the update!
Related topic
Hacker Leak more than 10,000 DELL EMPLOYEE Details Acer Data Invasion: Hackers sell 160GB stolen data DELL discloses data infringement.


